Employee Activity Monitoring
Most companies have antivirus and firewall installed. They provide decent protection for the network and computers from external threats, but are practically ineffective when it comes to employees, freelancers, system administrators, and other users.
Any organization possesses valuable data (for example, client databases, financial reports, supplier information, source codes, drawings, etc.). It only takes one insider for this data to end up in the hands of third parties or be openly accessible online.
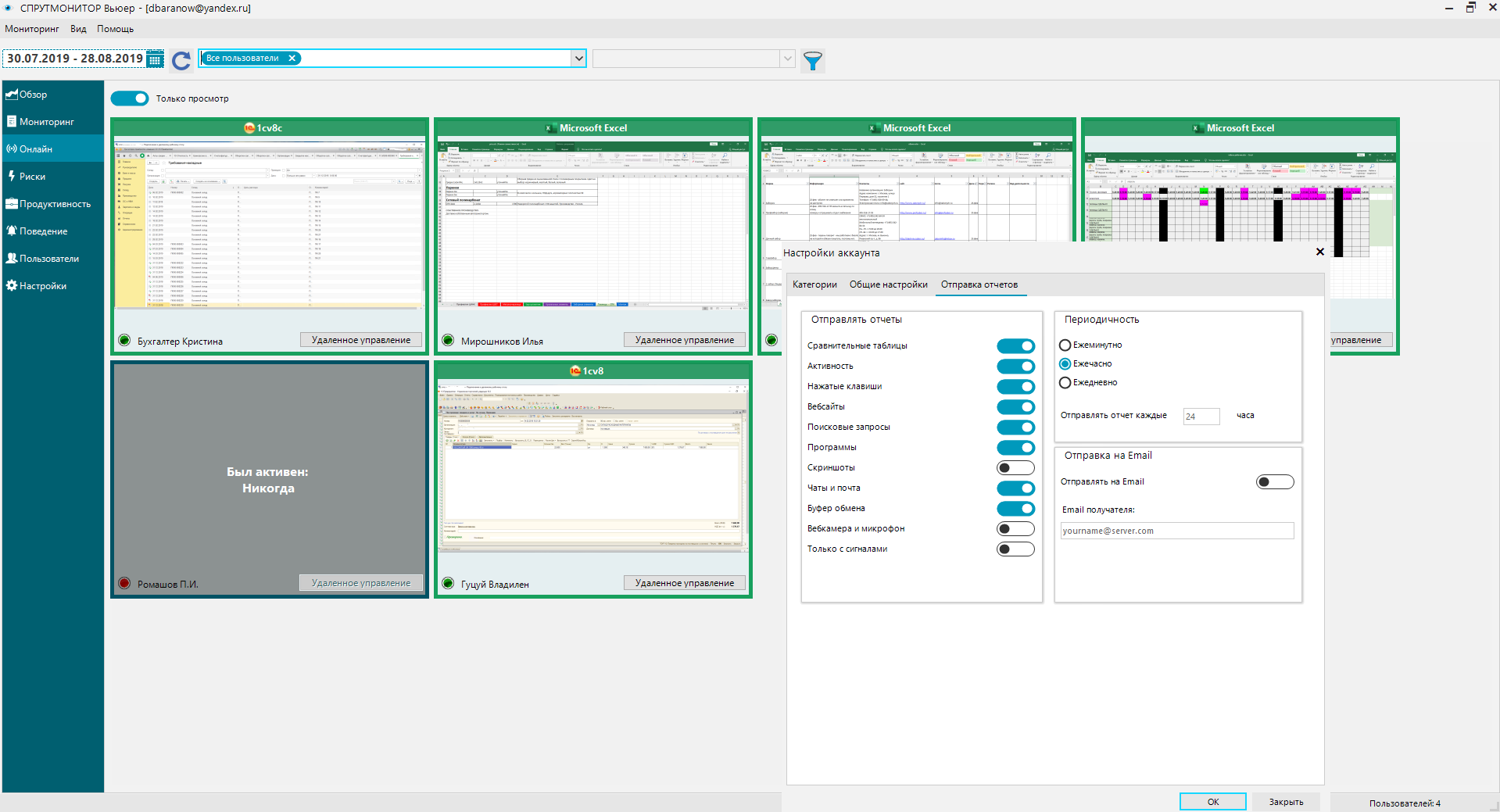
User activity monitoring is the process of tracking all actions and behaviors of users when they use a computer. A solution for employee monitoring helps ensure the security of confidential data.
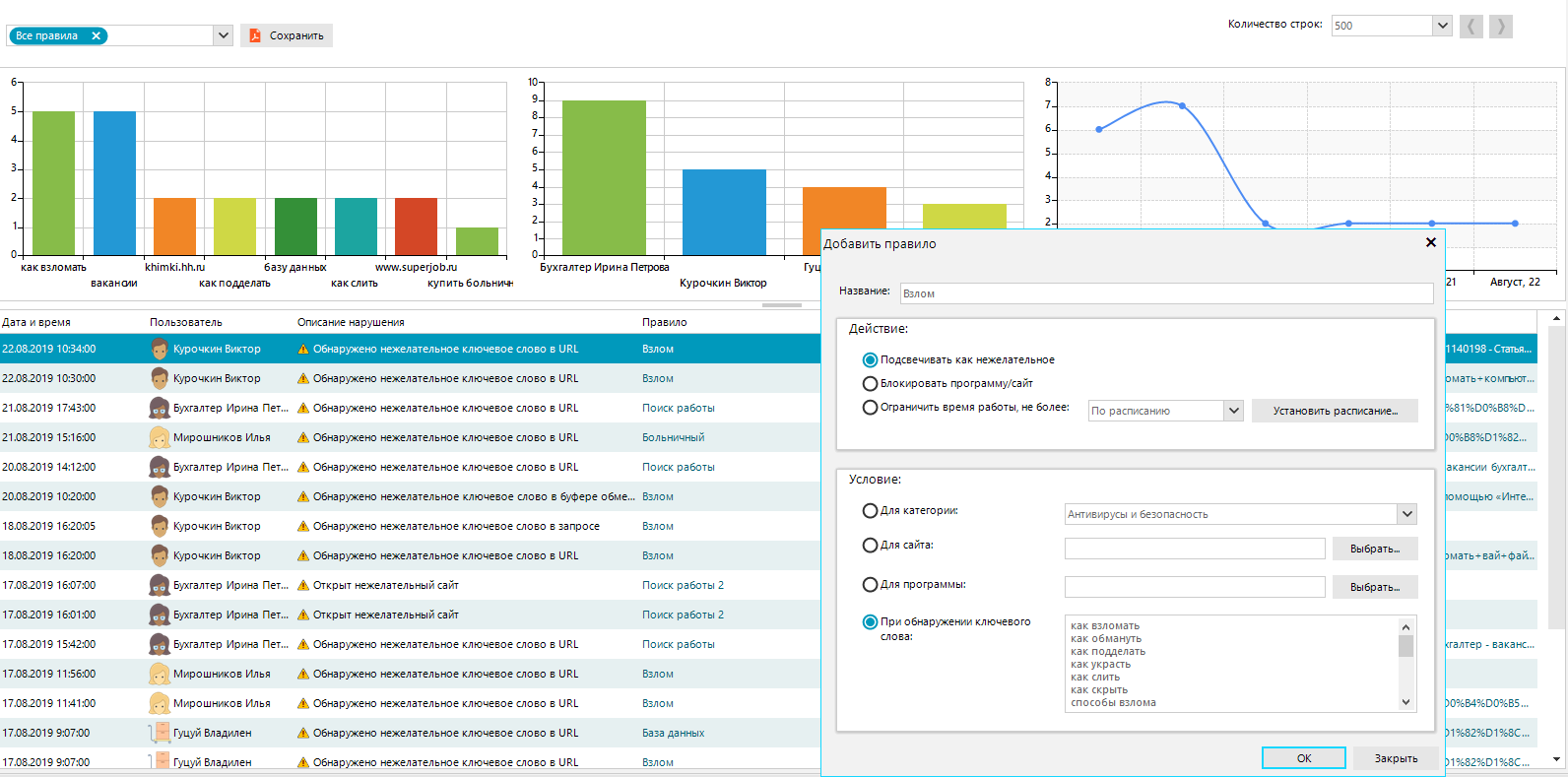
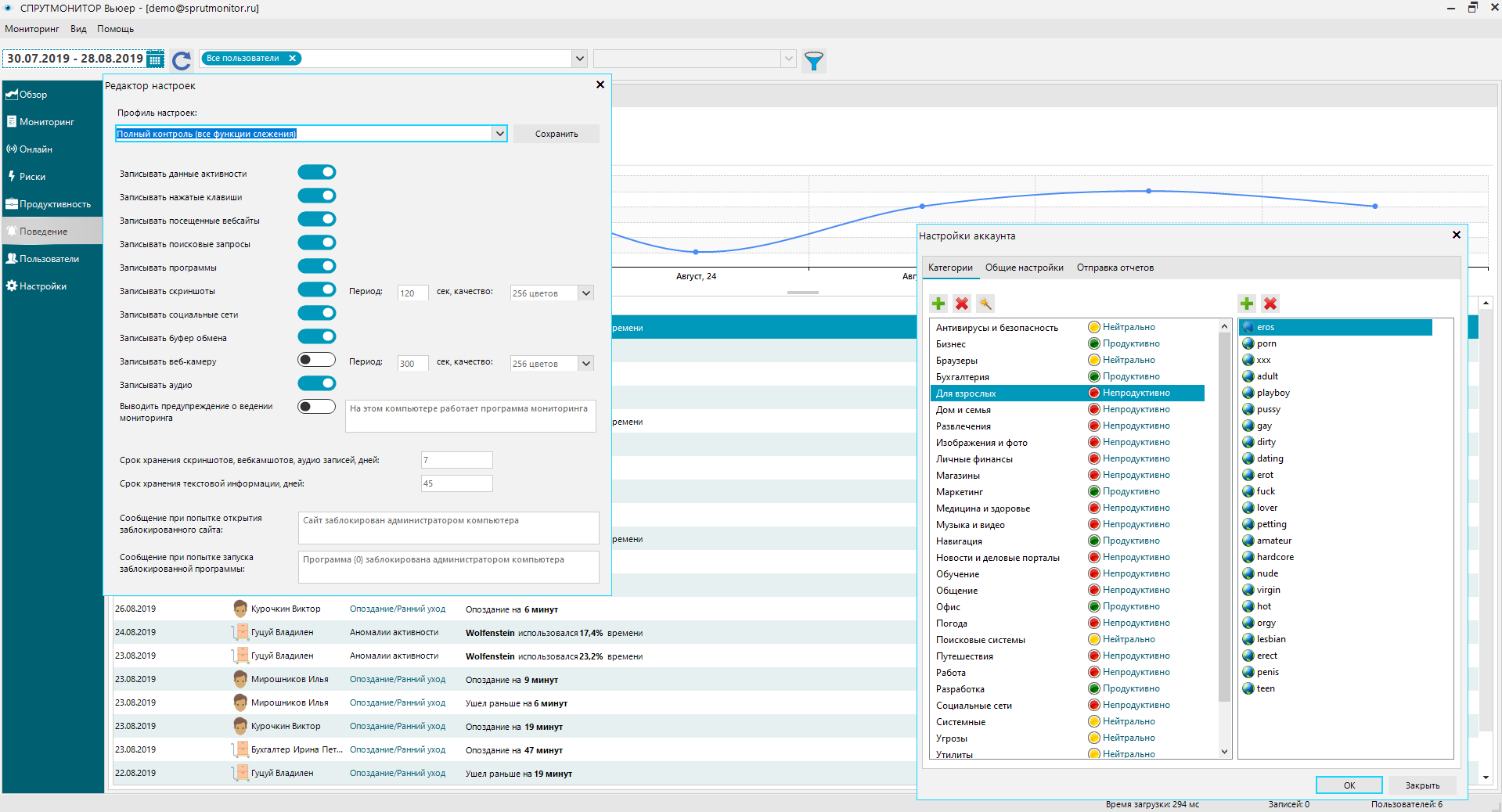
User activity monitoring system OctoWatch not only has the basic functionality of UAM systems but also has the capability to analyze user behavior (the system collects metrics, such as programs, websites, and files typical for the user; time of day; access level, and domain, etc.) and automatically respond to threats posed by employees (by warning, blocking users, blocking programs and websites).
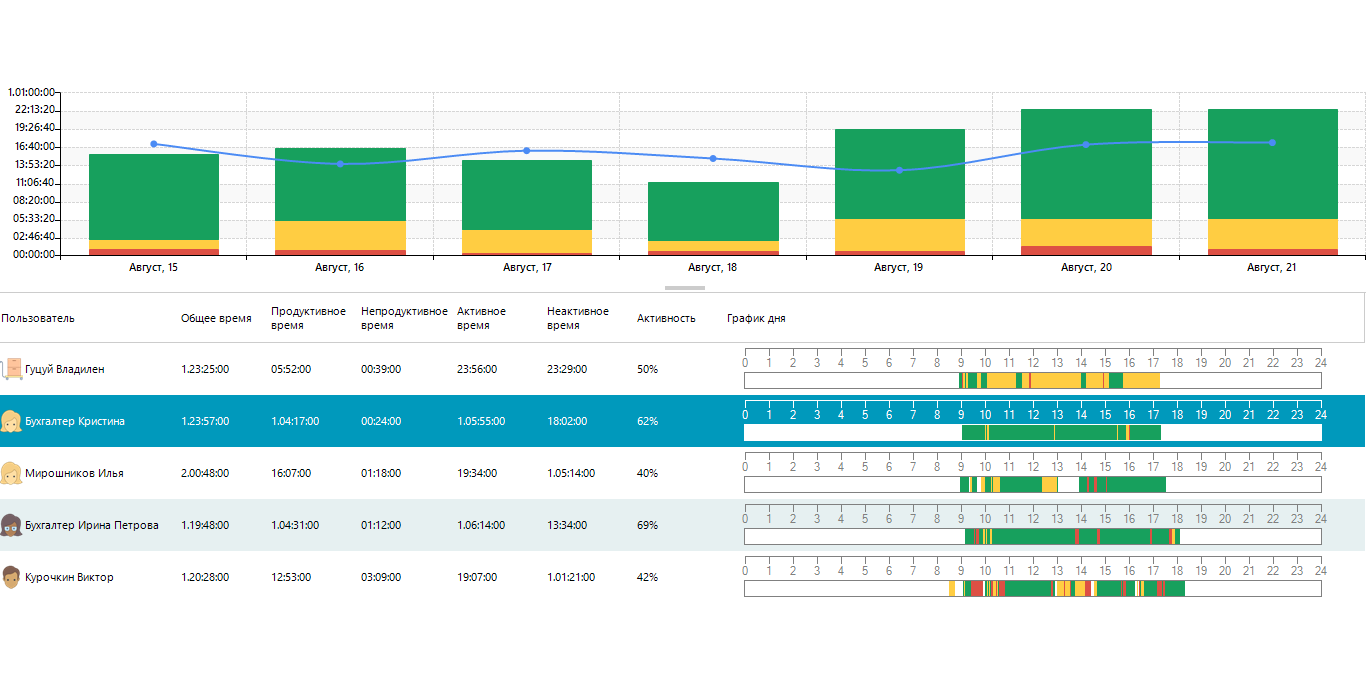
OctoWatch can assess employee productivity and risks. In the event of unauthorized access to data, OctoWatch will provide evidence of the intrusion to identify those responsible for the incident.