Insider Threat Detection
Every employee with access to information stored on the company's computers is a potential insider. The potential harm an insider can cause is classified as an insider threat. The confidential information most frequently stolen by insiders includes passwords, client databases, supplier data, personal information of clients, employee personal information, financial reports, etc.
Insiders have a significant advantage over external enemies: they are very difficult to detect.
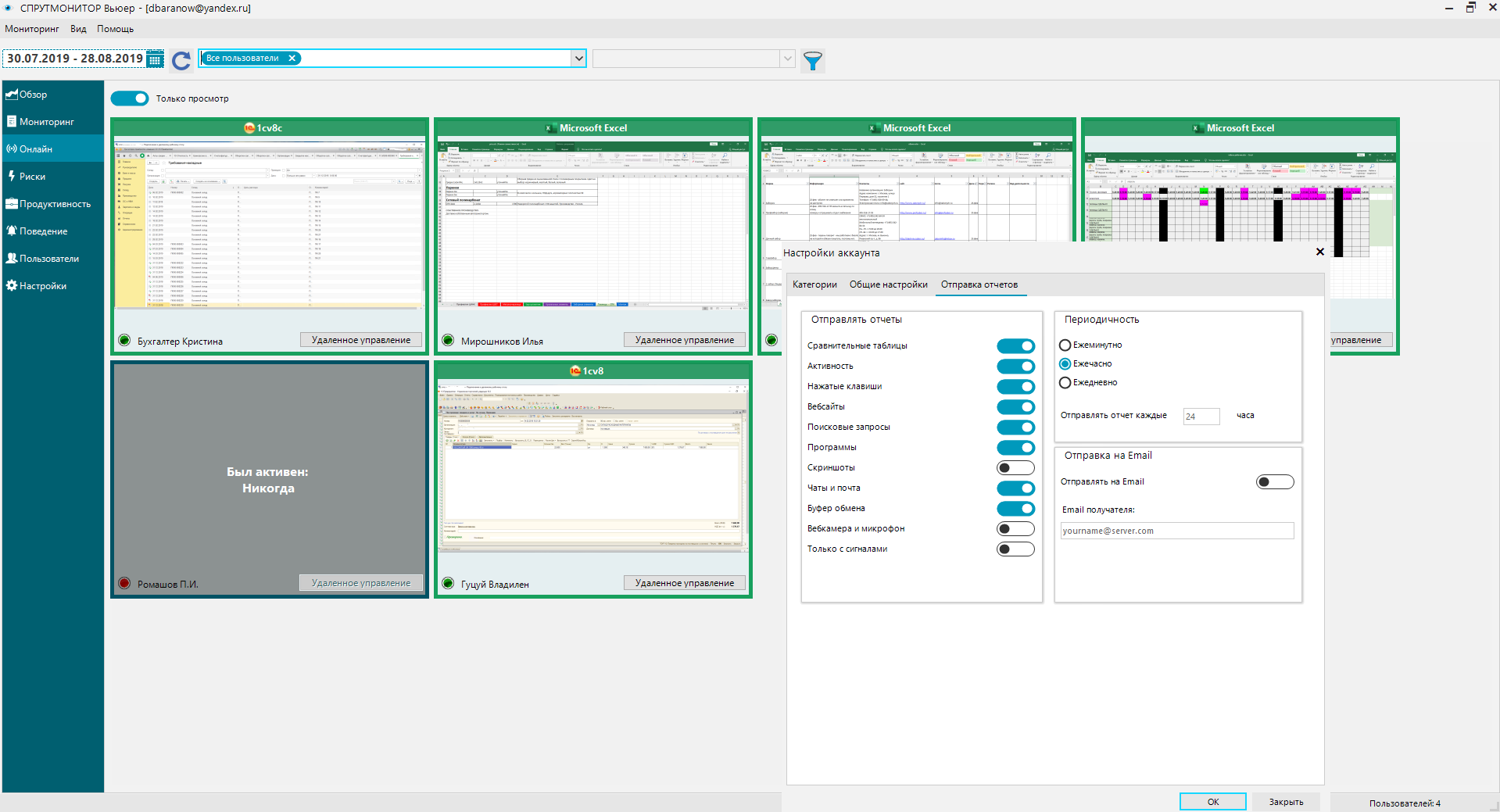
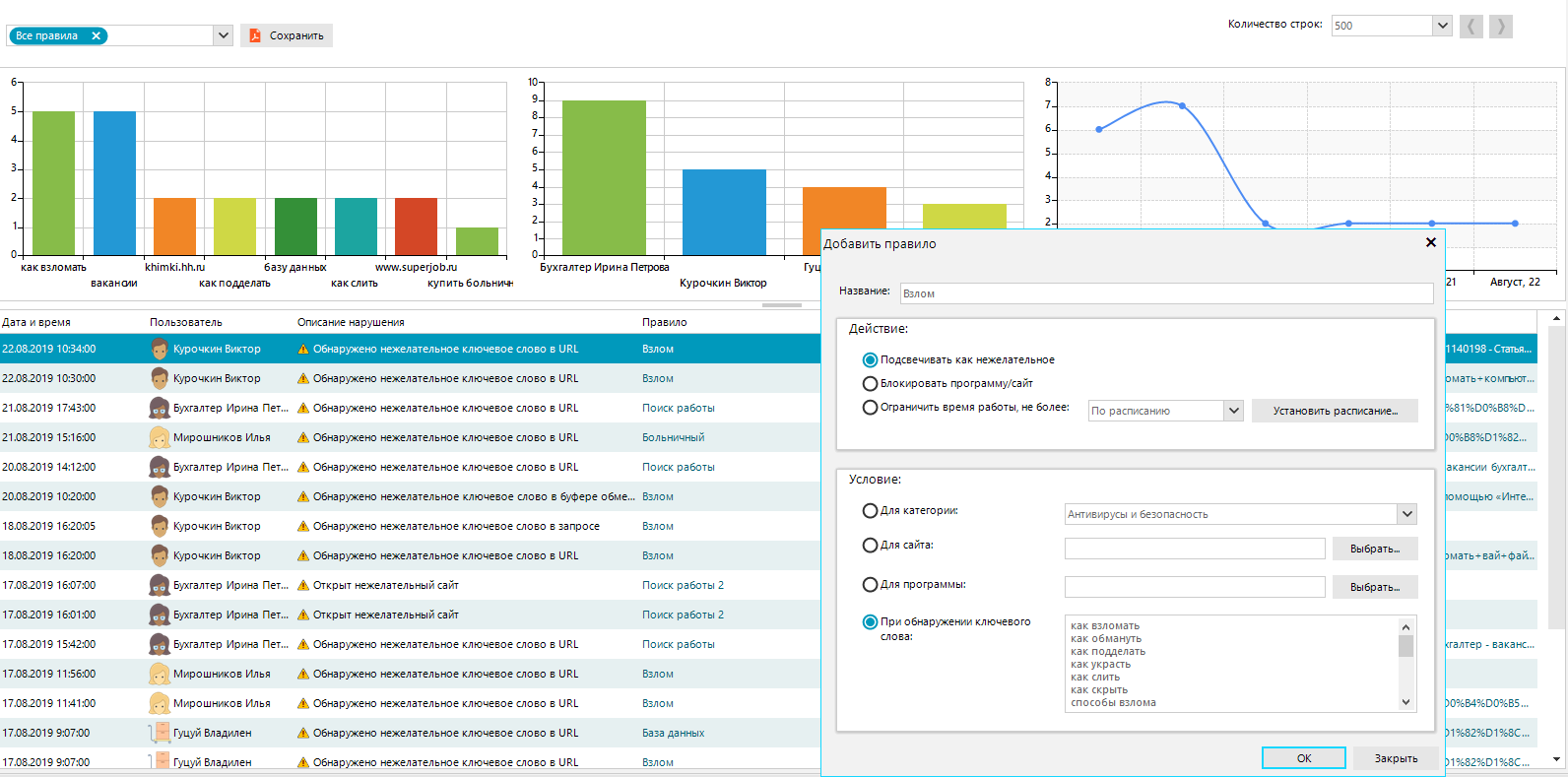
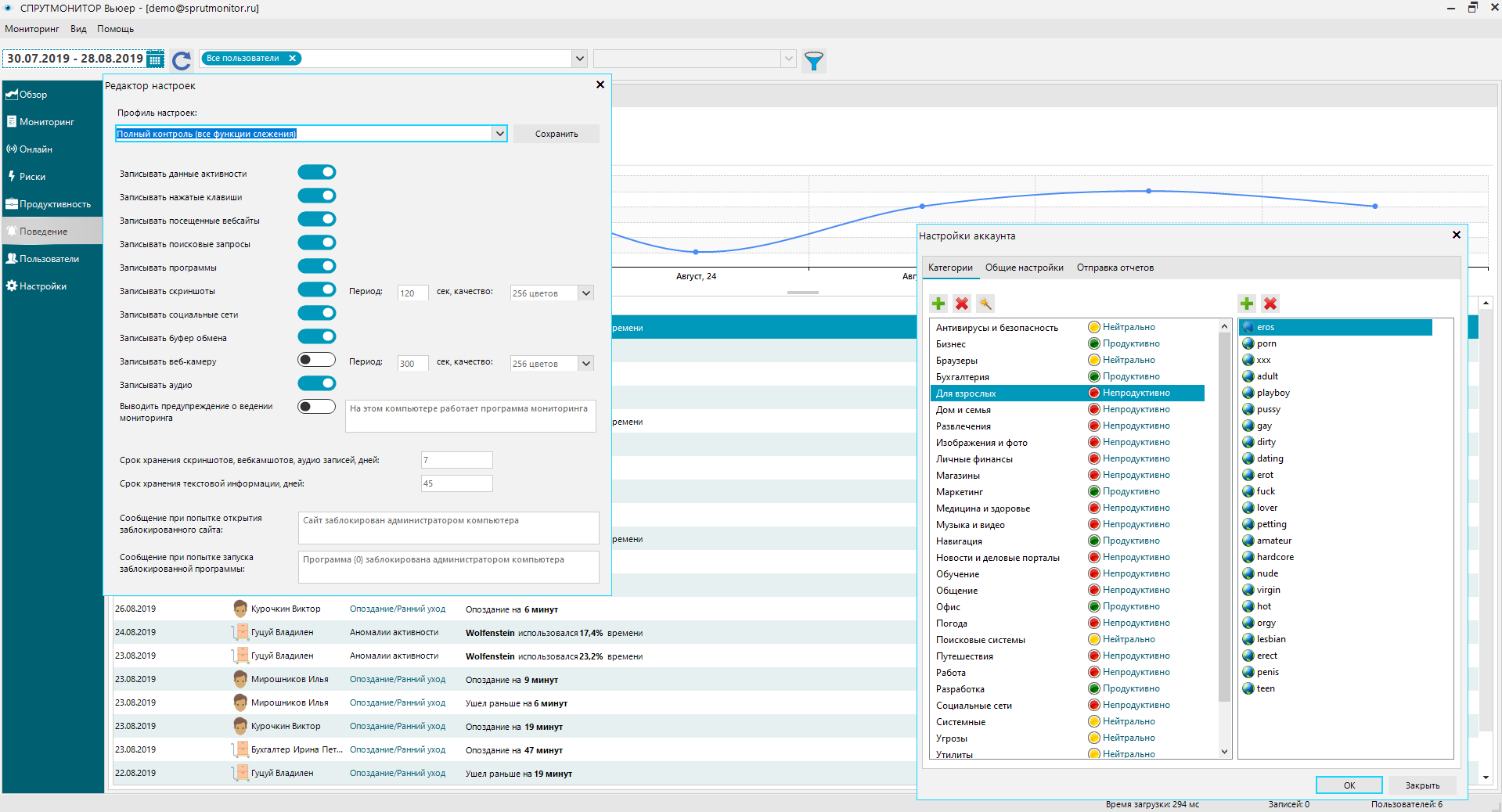
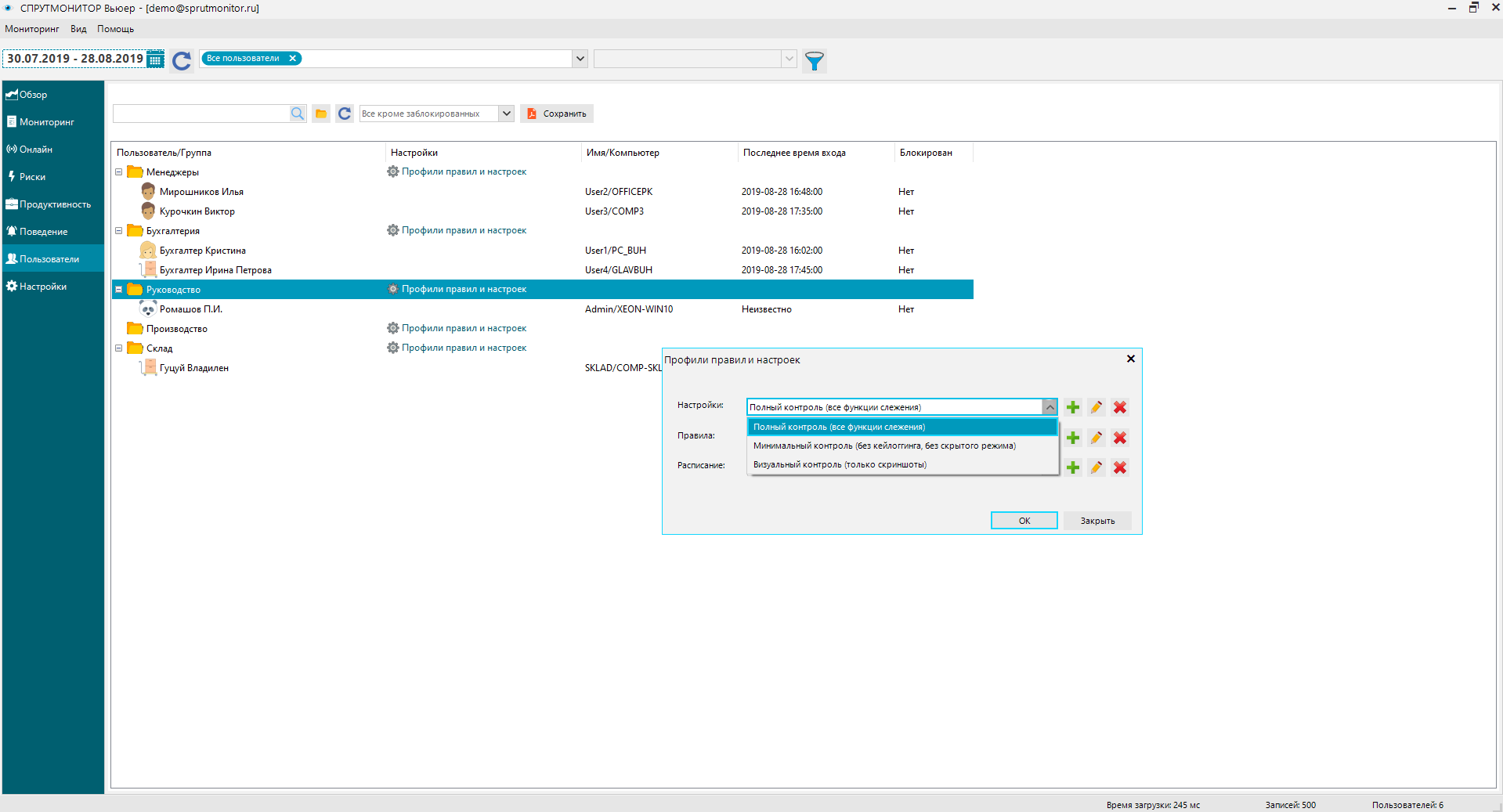
DLP system OctoWatch employs real-time monitoring of user actions to detect early signs of internal threats.
The rules system is configured to ensure active protection against all types of insider activities, such as data theft, fraud, industrial espionage, sabotage, and more.