Risk analysis and rules system
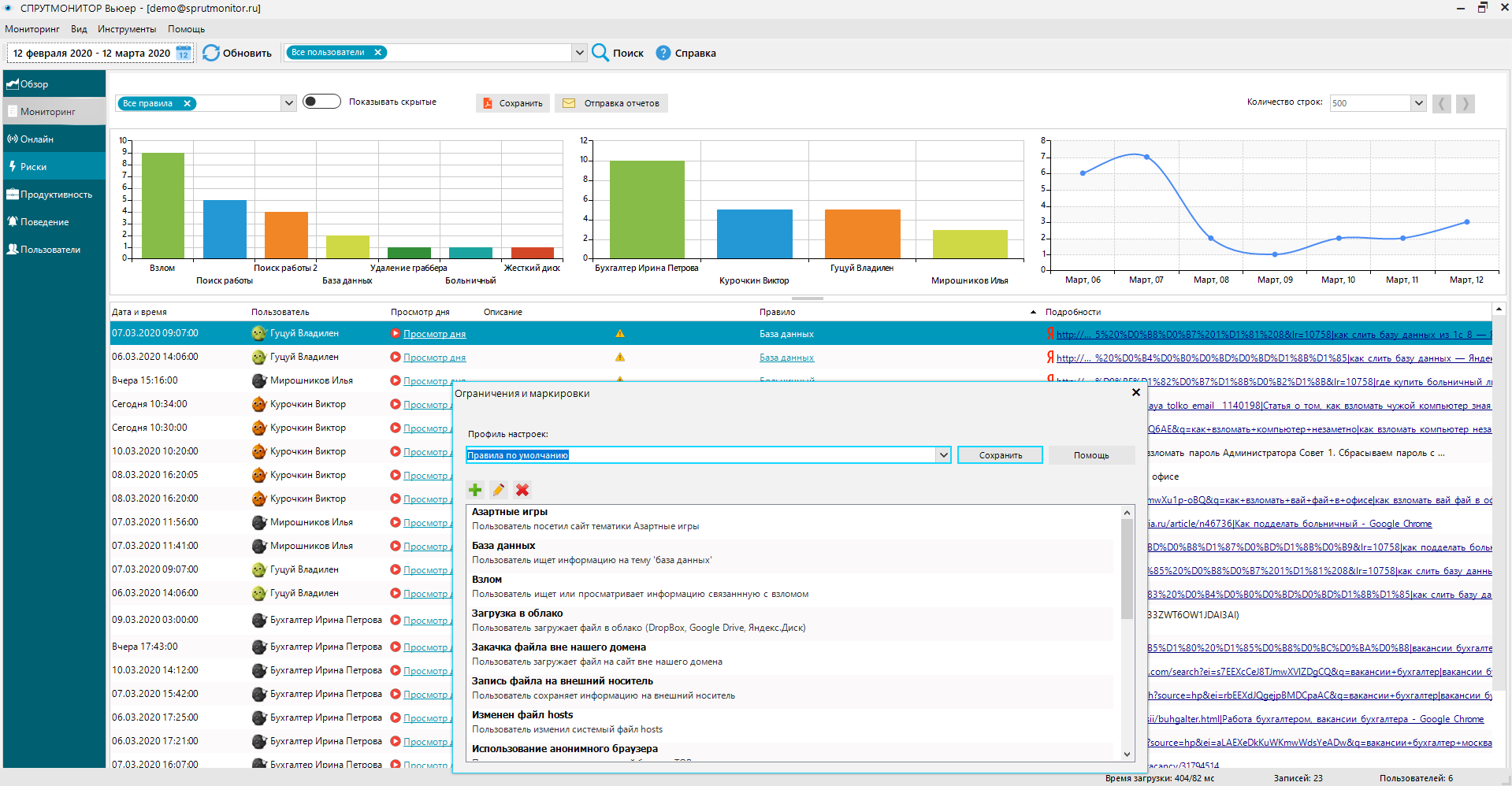
In OctoWatch, you can create rules to notify of risks or block certain actions. The rules system is an integral part of the OctoWatch software package.
Despite its powerful functionality, using this system is no more difficult than using regular office applications. Moreover, there are already rules included that we created as examples. A rule consists of two main parts:
- 1. A list of conditions. Examples: keywords in the URL, the name of the application, clipboard, window title, file or folder name, work time, day of the week, username, department, email attachment, key combinations, etc.
- 2. A list of actions. Examples: turn off the computer, send a notification, block reading or writing of a file, block removable media, block a site, close an application, clear the clipboard, etc.
Rules are combined into a profile that can be assigned individually to an employee or a department. The system already comes with a set of the most popular rules among our clients. Thus, the OctoWatch system will already notify you "out of the box" about situations when a user:
- Is not a human resources employee and sends an email containing a resume
- Uploads a file to cloud storage or copies information to a flash drive
- Works with an anonymous browser such as TOR, provides access to their computer to other users via TeamViewer, or downloads torrent files
- Spends more than 30 minutes a day on social networks
- Opens gambling sites, shows interest in drugs and "adult" sites
- Takes screenshots or prints out large documents
- Creates a password-protected archive
- Uses insecure channels to transmit confidential information (personal, personal data, commercial information, passwords, etc.).