How to Know if an Employee is Stealing
In this case study, we will examine possible methods of stealing intellectual information and other valuables that can be intercepted by using an DLP system.
If your organization does not have a warehouse, it does not mean that there is nothing to steal. Dishonest employees will always find something to pilfer. Managers are often interested in databases and customer information. Department heads and unit heads may be involved in bribery and industrial espionage. Supply department employees may look for kickbacks. Cashiers are drawn to cash. Accountants may be interested in the money in the settlement account. While the latter scenario is extremely dangerous and unlikely, the former are quite common.

What are the indirect signs of employee theft?
1. A Sudden Improvement in Financial Status
If a person previously complained about barely making ends meet and suddenly acquires a new smartphone/watch/computer/car, this should raise the interest of the business owner or HR manager.
2. Secrecy
Isn't it quite suspicious if one of your employees, standing out from the entire team, suddenly changes their account password, installs a VPN service, uses the anonymous TOR browser, copies documents to a hidden folder or to a flash drive?
3. Change in Behavior
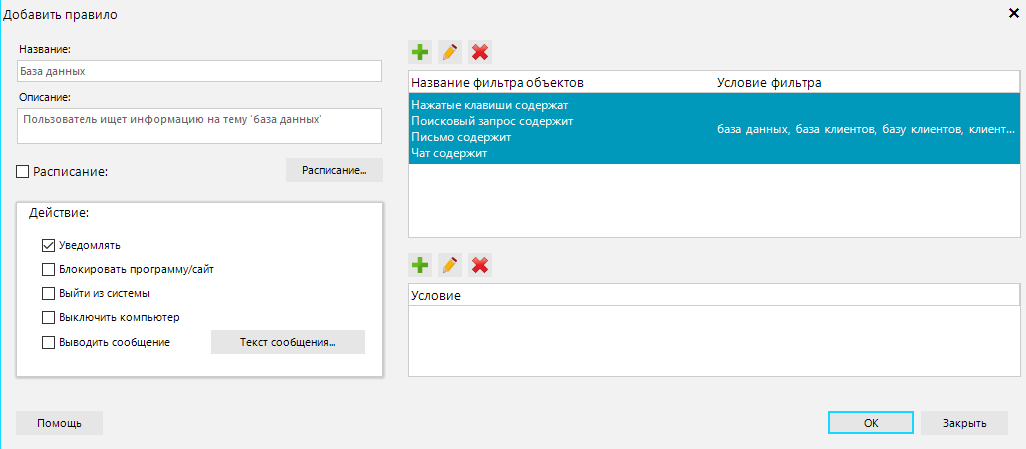
Using special software, anomalies in behavior can be detected. For example, an employee may have spent a significant portion of their workdays for a long period working in a text editor and CRM system. Then, suddenly, they begin to spend their days browsing travel agency websites, searching for trips. An appropriate activity monitoring system, such as OctoWatch, would immediately send a notification to the manager.
4. Absenteeism and Tardiness
If an employee has always exhibited low discipline, it raises questions about motivation and personal qualities. However, if the number of tardies, early departures, or even absenteeism suddenly increases sharply, this should definitely raise a red flag. Perhaps personal factors are to blame. But it's also possible that the person no longer values their job.
5. Friendship
Relationships within a team should be healthy. However, obvious friendships among employees often harm the company. Too many smoke breaks and tea gatherings reduce productivity. But that is not the worst part. Collusion among staff may result in significant financial harm. For instance, a female accountant might collude with a security guard or warehouse worker to allow the removal of goods from the premises without proper documentation. Or a manager in league with a marketer might organize a mini-business for reselling leads to a competing company.

Successful Cases of Detecting a Thief with a DLP System
Case #1 - Theft of Applications
In a company engaged in the construction of buildings from light steel thin-walled profiles, only one manager, B, received incoming calls. The specifics of this niche imply a rather high cost of attracting a client. Thus, one application for building calculations from contextual advertising cost approximately 2000 rubles. The company's manager decided to install employee monitoring software, OctoWatch. The program was installed on all computers in the company.
One of the functions of this program is periodic screenshot capture and optical character recognition (OCR). As a result, moments were recorded when the employee received, viewed (apparently photographing the application with a mobile phone), and then deleted the incoming application for building calculations. It was very easy to extract screenshots containing evidence of receiving the application thanks to the keyword search feature in the OCR results.
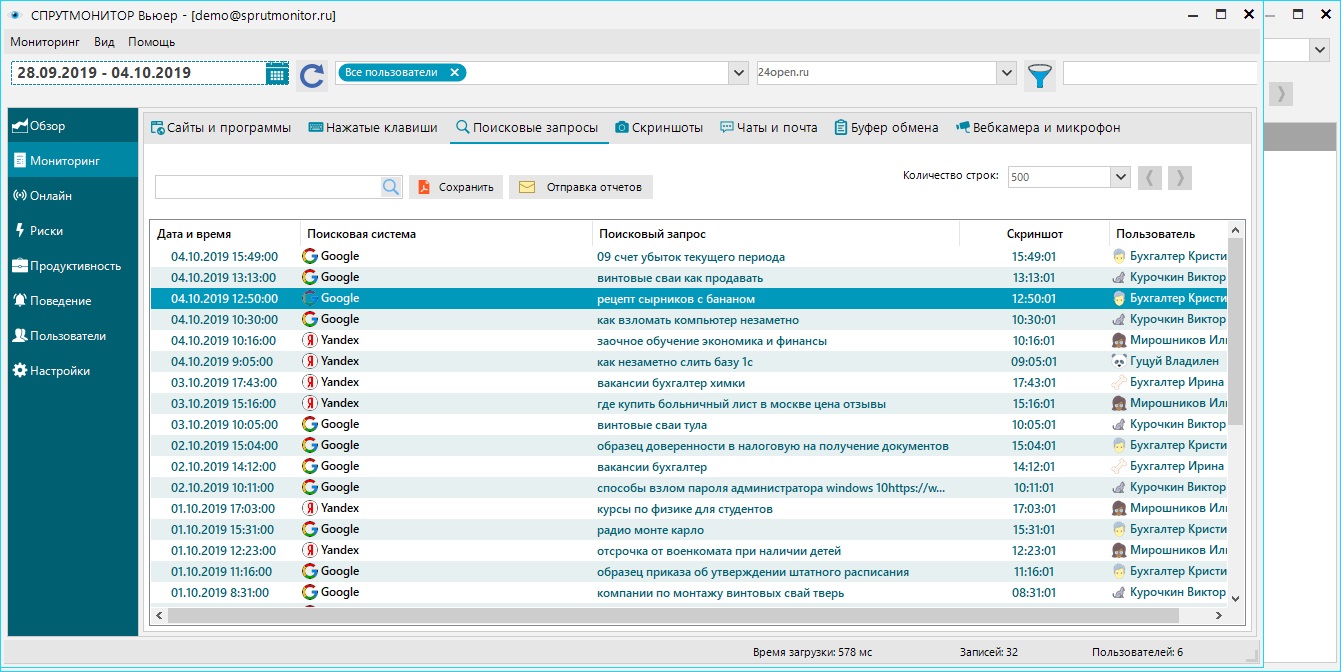
Case #2 - Attempted Theft of a Database
In a company engaged in wholesale sales of thin-walled profiled products, the sales department consisted of 6 people. The personnel control system, OctoWatch, was installed on the computers since the company's inception. The customer database was maintained in the 1C Enterprise 8.3 program, with the ability to export information to a file blocked by the system administrator.
OctoWatch comes with a standard set of keyword markers. The manager, N, configured email notifications to be sent upon discovery of certain words, and additionally, OctoWatch blocked access to cloud storage services like Dropbox, Yandex.Disk, etc.
One day, manager N received a notification that the keyword "database" from the list was detected on the screen of sales manager C's computer. At that very moment, manager C was performing the following actions: he created a folder called "database" (the rule triggered on these keywords), where he saved screenshots of the contact table of clients (as he could not export it to any file). Then he created an archive with these files and tried to access the file upload page on Yandex.Disk. At that moment, manager N received a second notification about the attempt to open a blocked website. Manager C did not know that uploads were blocked and, not having more time for a second attempt, deleted the archive with the files in hopes of hiding his actions. As you might have guessed, this was pointless, as all actions had already been recorded in the form of screenshots.
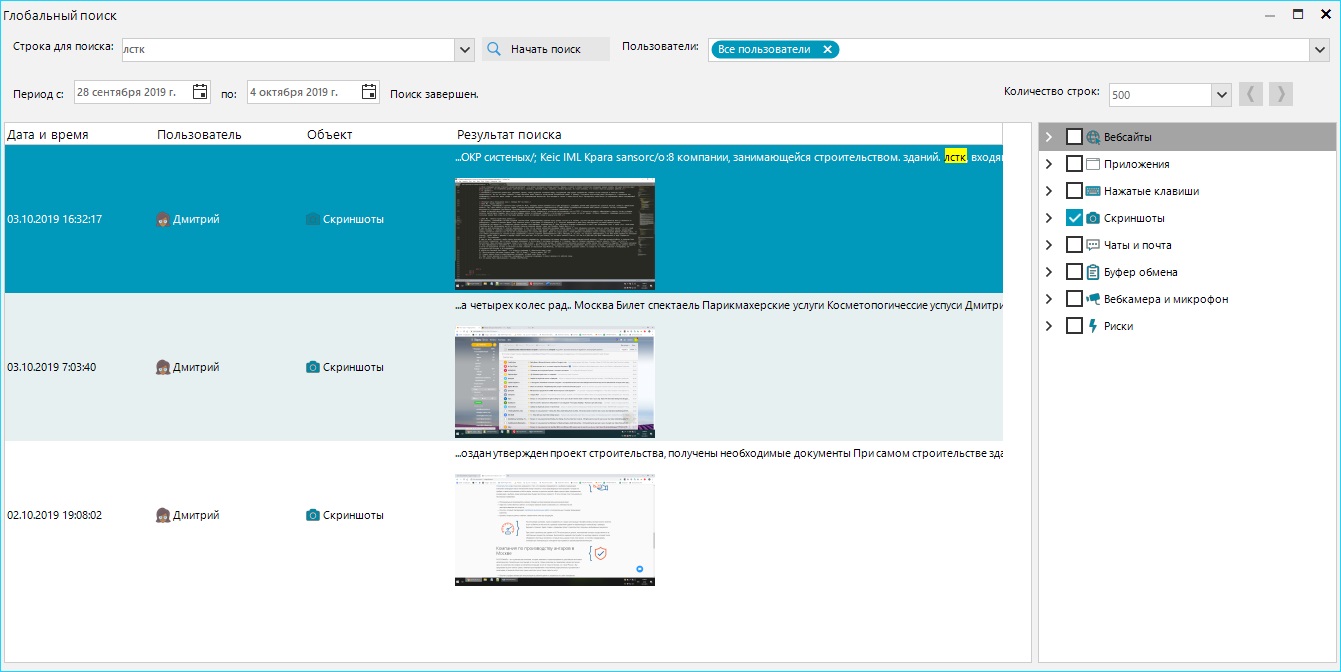
Case #3 - Investigation
The head of the security service of a manufacturing enterprise, while reviewing expense invoices, discovered a suspicious document. The document flow structure at the company was quite standard: when shipping, the manager requests 2 expense invoices and 2 waybills from accounting. One of the waybills is given to the client. The other remains in accounting. One expense invoice is handed to the warehouse, the other to security upon exit. Due to several external signs, the head of the security service was able to identify a forgery. The expense invoice was not generated in the 1C program but was simply "drawn" in Word. Naturally, the document number was also fabricated. The next task was to identify the author of this counterfeit. If a personnel tracking system, OctoWatch, had not been installed at the enterprise, this would have been quite difficult: at that moment, there were 5 managers, 10 accounting staff, and 14 warehouse workers at the factory.
As a result, the culprit was found - it turned out to be warehouse worker R. The evidence included:
1). Numerous search queries such as "TORG 12 blank", "download TORG 12 template".
2). Screenshots of the editing process that took more than an hour.
3). Fact of printing the document on a printer located in the warehouse worker's premises during their shift.
All this data was recorded using OctoWatch.